Fake messages sent out in our name

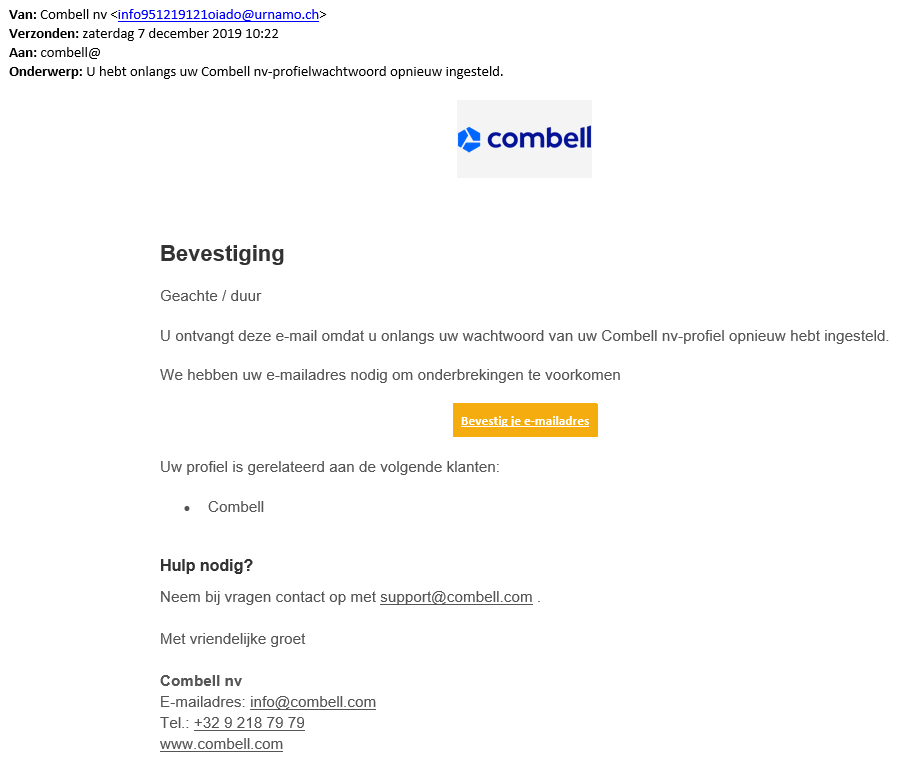
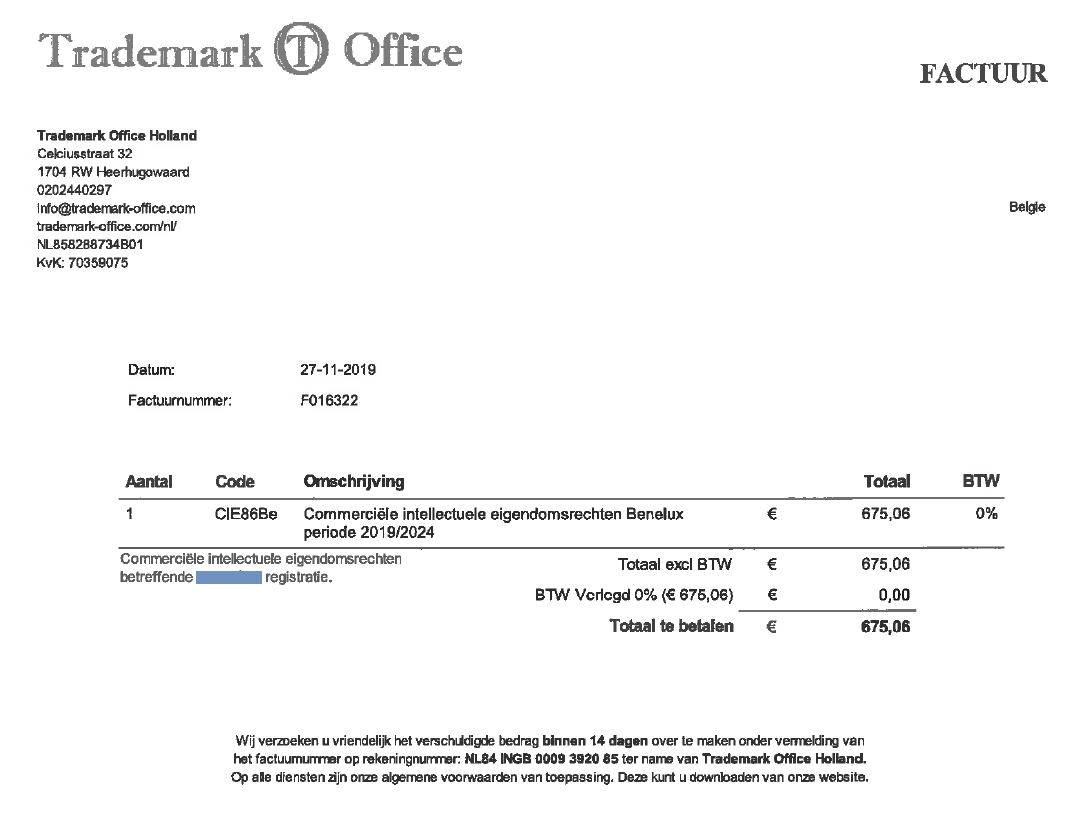
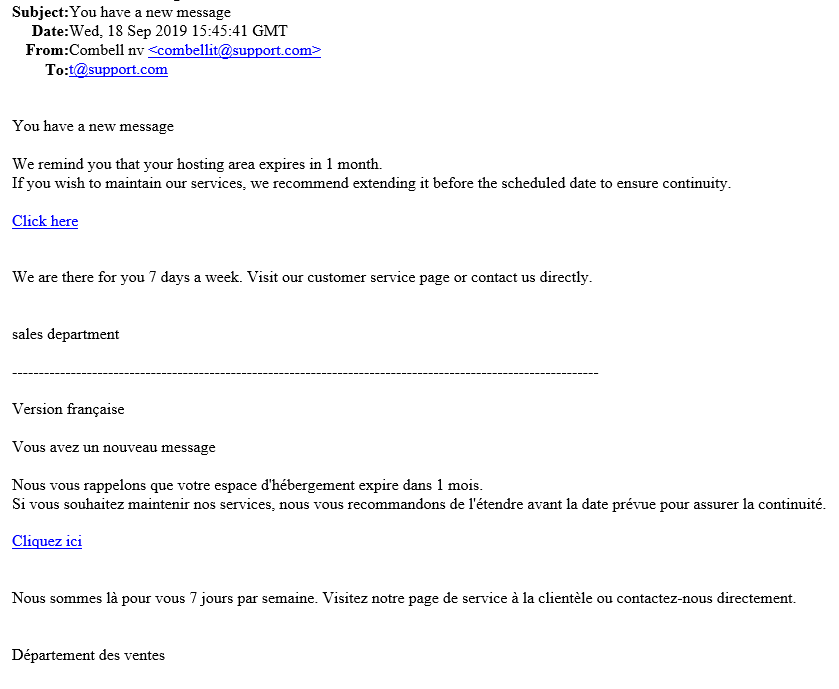
On a regular basis fake emails and text messages are being sent out in our name to some of our customers. In this emails and text messages recipients are prompted to log on or pay a fake invoice. In reality these are fake versions and the login details are sent off to individuals who undoubtably had bad intentions with it.
Because we value the security of our customers and their data, we would like to inform you further about this incident via this page.
Has Combell been hacked? The answer is NO
Unfortunately, several of our customers have already received phishing mails. Supposedly from Combell, but in reality from fraudulent cyber criminals.
"Has Combell been hacked?", "Is something wrong with your online security?", "Is my data safe with you?" … We get such worried questions from time to time. It's perfectly normal for observant customers to question these fake emails and/or text messages.. Because vigilance is key.
To answer those questions right away:
- No, Combell has not been hacked.
- Yes, Combell is still your ultra-secure and reliable hosting partner.
How did hackers get your customer data? Well here's how:
- Internet criminals use public data to send their mails to. If you register a domain name, then all the data linked to it is publicly available. This is data that even you and I can easily look up.
- Just surf to the WHOIS database to find out who owns a domain name.
- Hackers screen this database to see who uses Combell as a hosting company. This way, your domain name ends up in their mailing list of targets. There are even external tools that allow them to trace the personal email addresses of everyone in your company. Did you know they even try that through LinkedIn?
- Then the hackers send their forged but completely fraudulent emails to all "info@yourdomainname" addresses.
- Done: ping, you've got mail. A fake one, admittedly. As you can see, a security breach at Combell has absolutely nothing to do with this. No way!
As we speak, Combell is doing everything in its power to put an end to this wave of fraud. We investigate every report! In the meantime, protect yourself and your mailbox by reading the useful information on our website. On this page, you are already at the right place.
What should you pay close attention to?
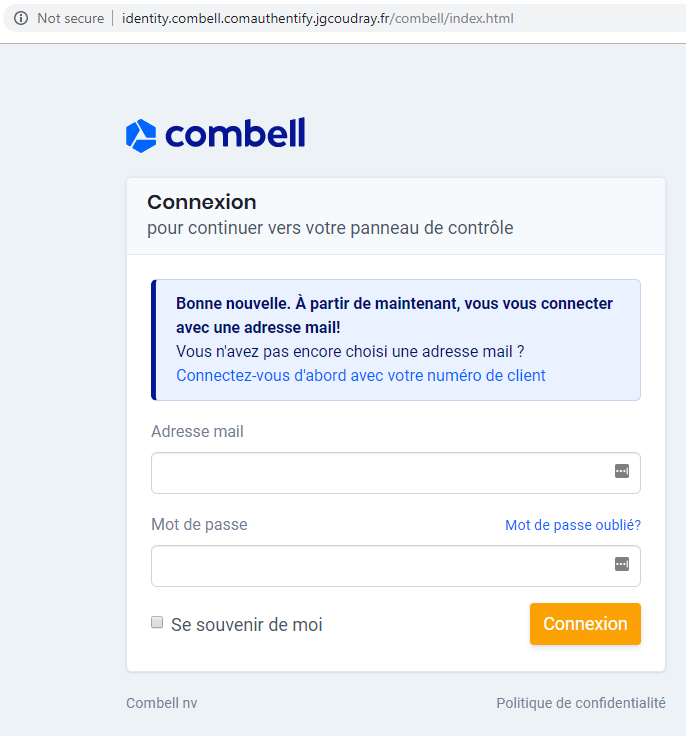
Always check your address bar before entering your login details. The correct URL you need to see when you are asked to enter your details always starts with https://identity.combell.com/login. Whether you access it via www.combell.com or via my.combell.com, this is the only correct URL for the login screen.

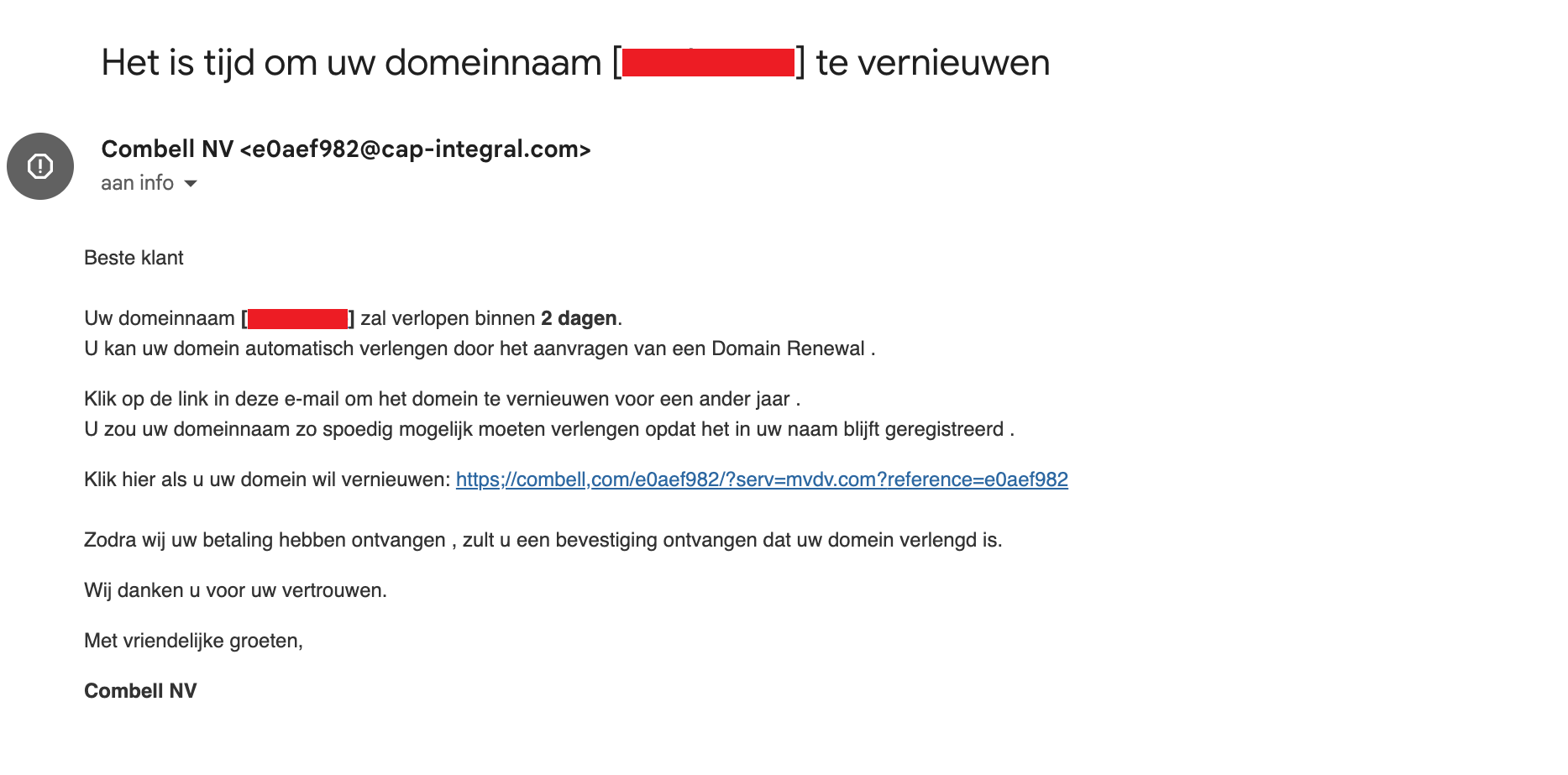
The right URL structure is very important. In a recent phishing attack, for example, the URL was http://identity.combell.comauthentify.jgcoudray.fr/combell/index.html. As you can see, part of the correct URL is often taken to make the fake URL as similar as possible to the correct URL. Always check that the URL starts with https://identity.combell.com/login and not a variant.

How can you avoid a phishing attack?
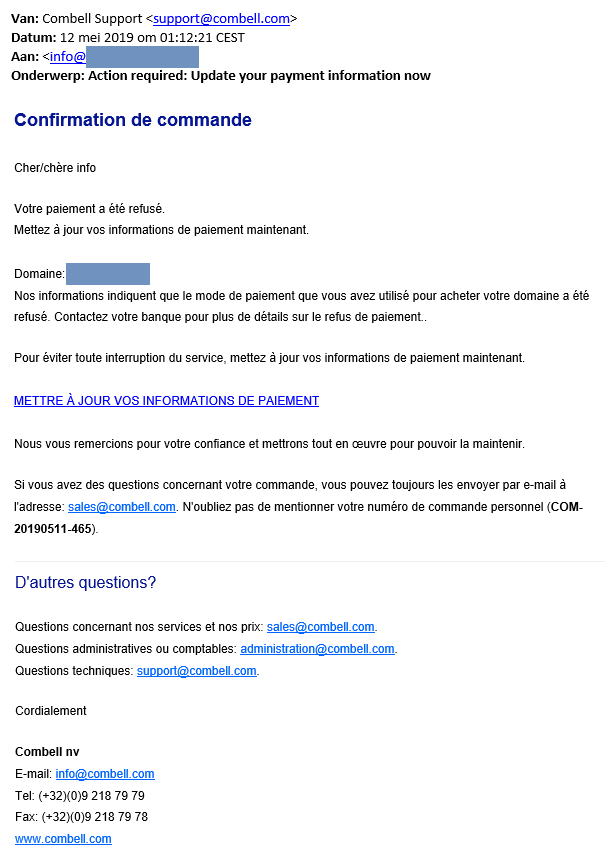
Below, you will find further examples of phishing emails and fake login screens so that you do not fall into the trap.
If you're unsure, don't hesitate to contact us. We know exactly which emails we have sent to you so we can quickly identify fake emails. If you need further information on these fake emails, or if you think you are a victim of this, please contact us as soon as possible.
More tips and tricks
Wat do you need to do when you left behind your login details?
- If you have received this email, clicked on the link and logged on with your credentials on this fake page, you need to take action immediately.
- You need to reset the password of the Combell account which you used to log on. You can do this via https://identity.combell.com/forgot-password.
- With your a-mail address and new password you can then log on again.
- We strongly advise you to reset all the passwords of your Combell users, and also all passwords of all products that you have with us (webhosting, FTP users, the passwords or your mailboxes, ...).
- We also strongly advise you to report this incident to support@combell.com. An engineer will inspect your account and might give you more tips and advice to securing your data even more.
- If you see it fit, you can also file an official complaint at your local police station.
What happens in a phishing attack?
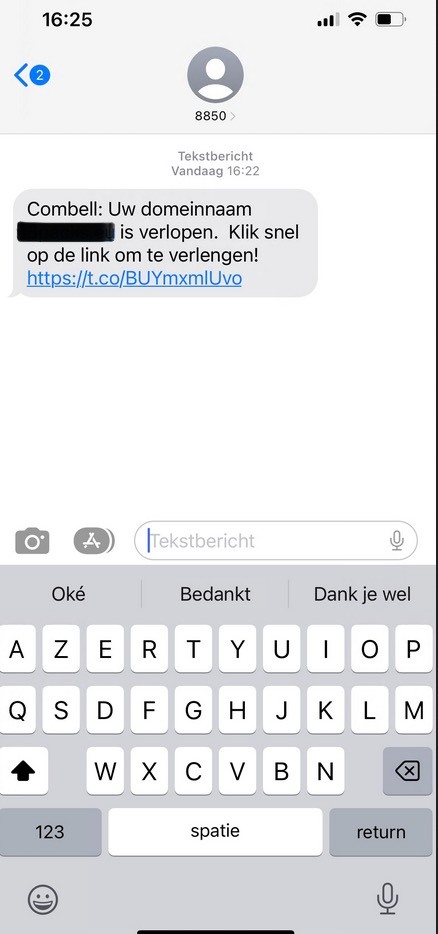
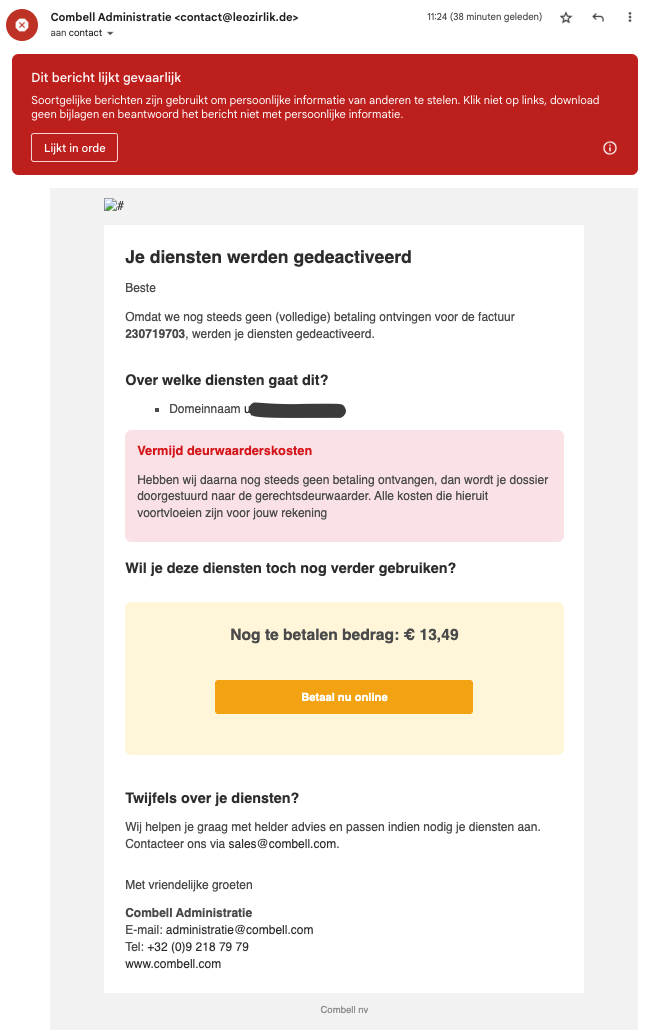
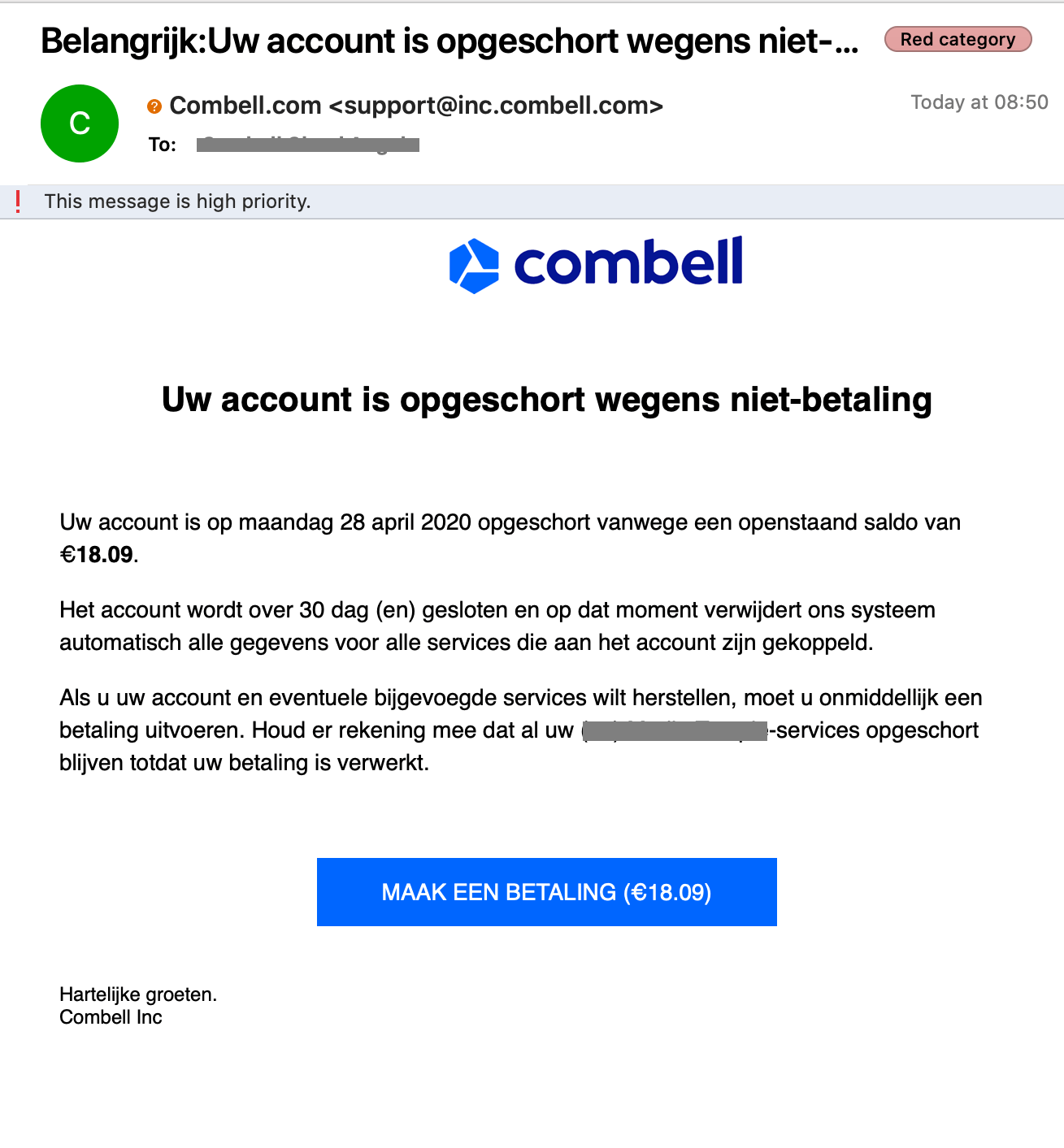
- Customers receive an email supposedly from Combell, informing them of irregular behaviour on their account.
- These emails were not sent by Combell but by a third party who used our logo and name to draft a so called "phishing mail".
- These emails were sent to random email addresses (info@, webmaster@, david@, tom@, ...) of domain names that are registered by Combell.
- The email prompted users to click on a link and log on to the Combell control panel with their customer details, to verify their identify.
- In reality, the visitor was redirected to a fake version of our website, which also was not hosted by Combell.
- When a user would log on to this fake website using his customer credentials, these credentials would most likely be sent off to a malicious person or organization. The details could then be used to illegally log on to a Combell account and alter or delete services and products, place fake orders, ...
What does Combell do about this situation?
- Combell takes every phishing report very seriously. It is important that our customers tell us what kind of fake emails are being sent.
- Depending on the number of reports, Combell can decide to inform its customers via social media or even via email.
- Contact is always made immediately with the company that was used to host the fake website or to send the emails. This means we can often take the fake websites offline within a few hours, but we are dependent on other web hosting providers to do so.
- Our spam filters are updated as soon as possible to immediately block fake emails on our own servers, should they be sent again.
- For additional security, we offer two-step verification for your Combell account. If your password ends up in the wrong hands despite all the precautions taken, your account remains protected by the second factor.
Examples of fake emails and text messages