What is a DDoS attack, and how can I protect myself from it?

DDoS attacks can cause major economic damage and completely shut down websites. What is a DDoS attack? How can you protect your website against DDoS attacks and what measures does Combell take to address this issue?
What is a DDoS attack?
(Distributed) Denial of Service-aanval
First, we need to explain what a DoS (Denial of Service) attack really entails. This is a situation where a computer system cannot provide the service that you are expecting as a user. This can happen due to an unintended error in the program, but usually these are situations where the access to servers, devices, services, networks, applications, or even specific transactions within applications is deliberately made impossible by e.g. computer hackers or activists.
Where there is only one system with a DoS attack that carries out the attack, the attack with a DDoS (Distributed Denial of Service) attack will come from various systems.
DoS and DDoS attacks have existed for more than 20 years. The first attack that made the papers goes back to the year 2000, when a student with the nickname Mafiaboy managed to shut down sites like Amazon, CNN and eBay. In October 2016 an important provider of Internet infrastructure services, Dyn DNS, was hit by a DDoS attack, so services like Amazon, Netflix, Reddit, Spotify, Tumblr and Twitter were disrupted.
Requests
In concrete terms, the system that is being attacked is flooded by a huge amount of data requests. For example, a web server can receive so many requests to show a page that it cannot handle this and becomes unavailable. The target can also be a database, which must process so many queries that it cannot cope, slows down or even crashes. As a result, normal requests no longer reach the database or data server, and the user is not shown the desired information. Ultimately, the fake requests fully utilise the available bandwidth, CPU and RAM.
Too much traffic = traffic jam
During a DDoS attack, it is exactly as if countless people wanted to simultaneously visit a website or request something from a server. The only difference is that these people are not real persons, but rather 'bots' that are part of a botnet. Learn more about this below…
A DDoS attack can be compared to a traffic jam. If countless people suddenly decide to hit the motorway at once, all the vehicles will end up moving very slowly. And the same goes in the case of a DDoS attack: an attacker uses bots to obstruct the Internet traffic to your website.
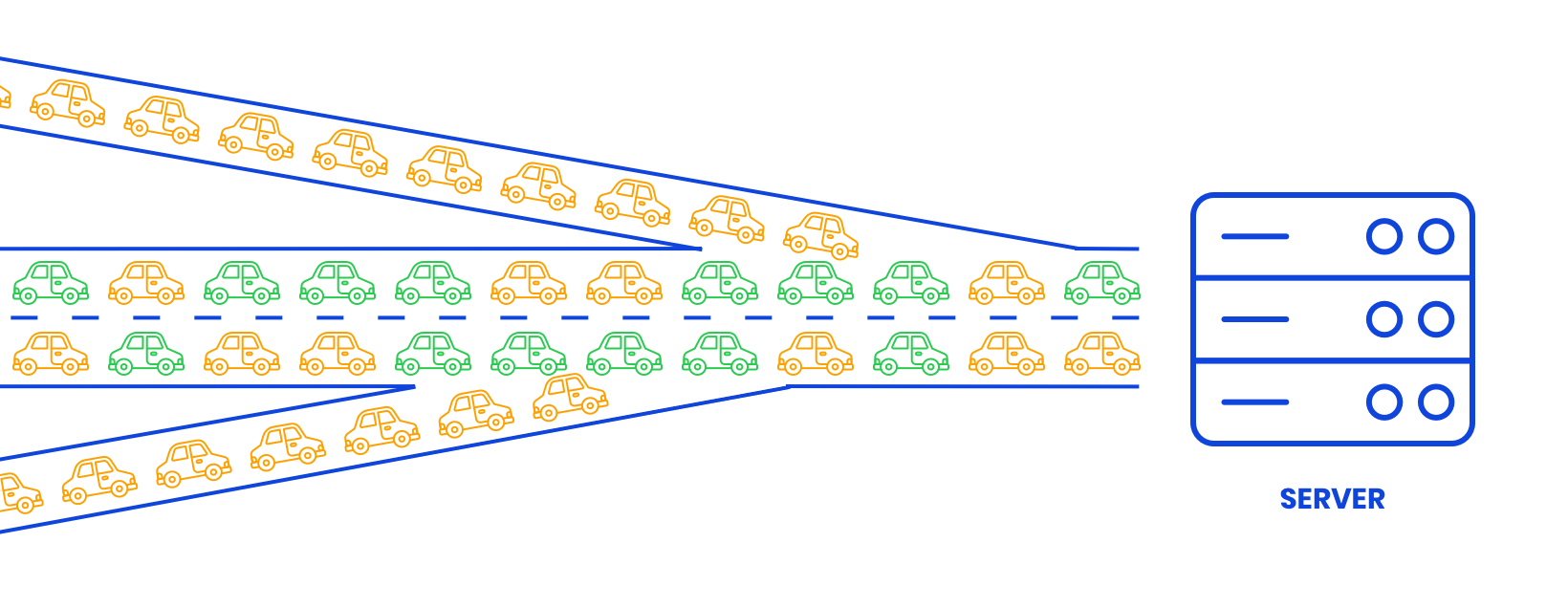
The consequences of a DDoS attack
Hacking vs. DDoS attack
It is important to know that there is a difference between hacking and DDoS. Hacking usually involves a hacker stealing your sensitive or critical data in order to extort money from you or sell your data to other hackers.
During a DDoS attack, your attacker floods your server with a massive amount of requests, but cannot access your secure data. Data theft is therefore usually not the reason behind such attacks: the attacker simply wants to cause you inconvenience by having your servers dramatically slow down.
The main consequence of a DDoS attack is therefore that the target's systems become incredibly slow. And this can of course be quite problematic for companies or organisations whose applications and databases need to be easily accessible, such as banks or hospitals.
What is the role of a Botnet in a DDoS attack?
The attacks, however, are becoming more powerful. At the end of the nineties, 150 requests per second were enough to crash a system. With the attack on DynDNS, this amount had grown to 1.2 TB of fake requests per second. The most severe DDoS attack to date was one launched against Amazon, with traffic reaching a volume of 2.3TB (!) per second.
The impressive amount of fake requests, originating from various sources, is only possible by using ‘botnets’. These are computer networks on which the hackers have installed software, unbeknown to the owner, which suddenly comes alive with the attack. These are also called zombie computers, who listen to the botnet-shepherd. For example, the Mirai botnet was used with the DynDNS attack, which worked with more than 100,000 IoT devices, IP cameras and printers included.
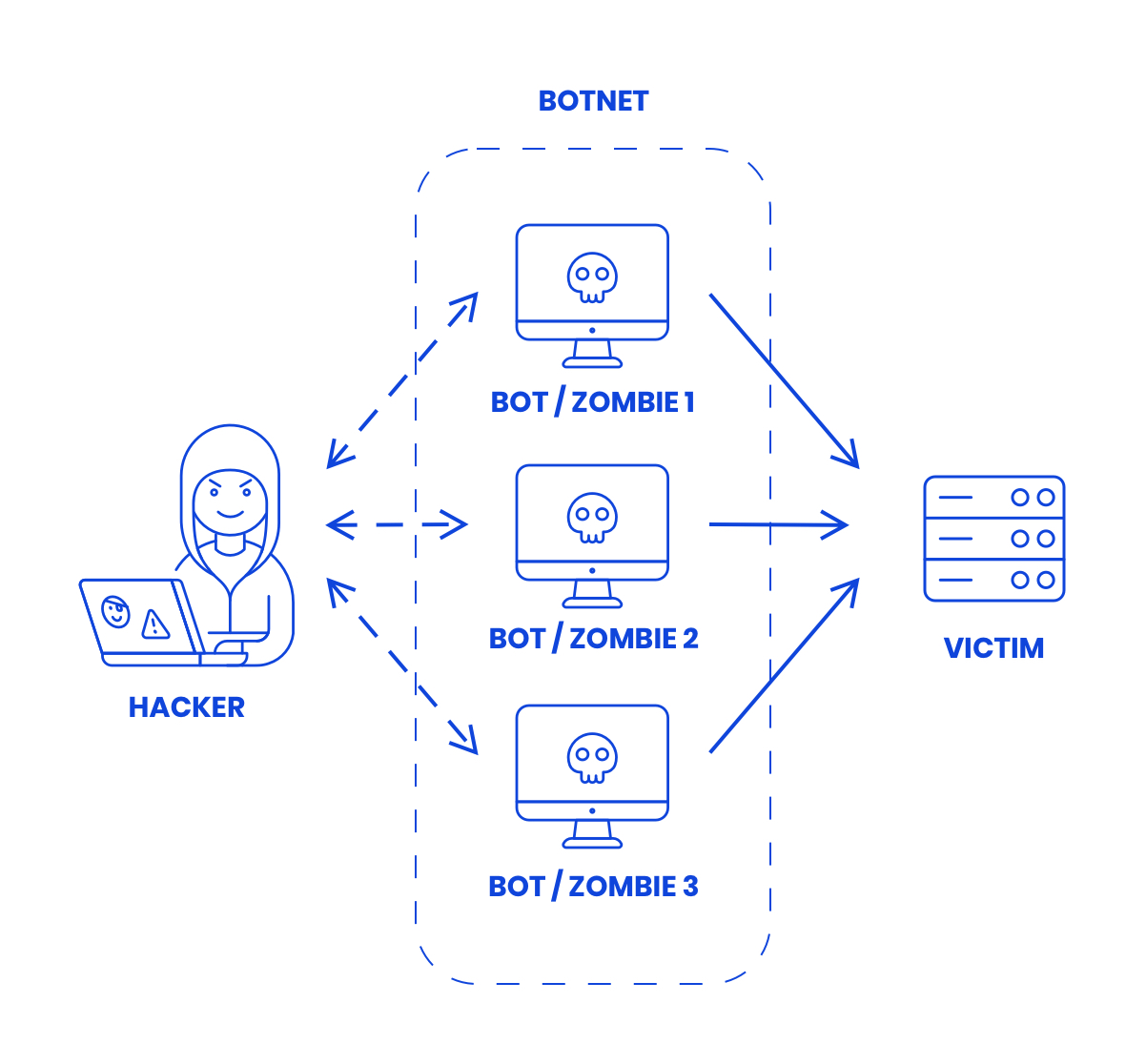
Such botnets are cynically enough for sale or rent on the Dark web, ready to be used!
If you would you like to find out more about the different types of DOS attacks (such as Syn Flood, UDP Flood, Ping of Death, etc.), this article published on eSecurity will introduce you to this dark world.
Who carries out DDoS attacks and why?
Why would someone carry out such an attack, you might wonder? The answers vary… Some do it ‘just for fun’, because they can; by doing so, they like to establish a reputation as a hacker. Others have downright criminal purposes, such as extortion. They attack a website and demand money to stop the attack. And with that one successful attack, they can threaten other companies: “pay or the same will happen to you!” It is a bit like mobsters and their ‘protection money’. These attacks may also involve individuals, with personal reasons, or a group. Government-sponsored attacks against systems of other countries are also possible.
Your attacker may also be seeking to damage your reputation, or may not agree with the ideas being promoted by your company or government. There have even been cases of DDoS attacks against college websites. Perhaps it was the work of a student who did not feel like going to class on a Friday morning 
What does Combell do to protect you against DDoS attacks?
To start with, Combell has a major advantage: its network is very extensive. Where attacks on servers with smaller hosting companies would immediately bog down the network, the traffic of the fake requests can be distributed across the large network at Combell. Imagine a single lane, which is suddenly overwhelmed by a lot of traffic so the traffic stops completely, and then a road with 100 lanes, that can smoothly process the increased traffic. In other words, capacity is a key factor.
Furthermore, Combell has implemented different defence mechanisms to detect DDoS attacks in time and to respond immediately. An additional option that Combell offers you, is our automatic scrubbing service. With this, we check all the traffic that comes into our systems. If any incoming request smells like DDoS, we immediately redirect it. This way, legitimate traffic can continue to get through smoothly, while the 'bad' traffic is 'stuck' somewhere else and does not inconvenience anyone. This way, even if a DDoS attack is underway, your visitors will still be able to access your website or application without any problems.
In the video below, one of our Chief Technology Officers, Wesley, explains what Combell does to counter DDoS attacks.
Protection against DDoS attacks is only one of the security measures taken by Combell
Conclusion: the economic damage that is caused when a website or web service is temporarily unavailable as a result of a DDoS attack can be enormous. The technology of DDoS attacks is coming more and more advanced and requires an increasing higher level of vigilance and protection against the attacks. The experienced collaborators of Combell closely follow these developments and apply the latest defence mechanism as soon as possible. So, you can be assured that your website will remain available.
Combell Shield
In addition, Combell also takes many measures to guarantee the protection of your website or services in all other areas. This way, the people who use our web hosting can be safe behind our Combell Shield, which is a collection of defence systems.
Also discover
Service Level Agreement
You can also rely on the special protection mechanisms offered by Combell for other hosting services, such as tailored managed hosting. In your Service Level Agreement, you can also include options like security audits, security tests and stress tests. Check out the options available with our SLAs.
Physical protection
And last but not least, the final piece of this protection is the Tier 3+ data centre where your hosting is located. Not only is it a robust building, resistant to water, fire and power failures, but it is also strictly guarded. In addition to the strict access control system, the data centre features 24/7 physical security and continuous video surveillance.
You can rest easy, Combell stands guard 😉!


